LinkedIn, the world’s largest professional networking platform, has a bot problem. As the site’s popularity continues to grow, so too do the legions of bots and fake accounts plaguing the network.
But what exactly are LinkedIn bots? How can you spot them? And how can genuine users protect themselves against these automated imposters? This comprehensive guide has got you covered.
Table of Contents
What are LinkedIn Bots?
A LinkedIn bot (or social bot) is an automated software program designed to mimic real human behavior on the platform. Bots can perform various functions without manual oversight, such as sending connection requests, liking and commenting on posts, joining groups, and sending messages.
While some bots can be benign or even helpful, many exist solely to distribute spam, scrap data, inflate social proof, and otherwise undermine the integrity of the LinkedIn environment.
LinkedIn Bot Categories
LinkedIn bots can be grouped into three main categories:
1. Spam Bots
Spam bots attempt to spread malicious links or unwanted content on LinkedIn via bogus comments, messages, and invitations. Their goal is to drive traffic to external websites for financial gain.
Common spam bot activity includes:
- Commenting irrelevant/spammy content on posts
- Sending connection requests with suspicious messages
- Messaging spam links for phishing/malware
2. Scraping Bots
Scraping bots systematically harvest LinkedIn user data (names, job titles, companies, etc.) to build marketing databases. This data may be sold to third parties without consent.
Scraping bots often have minimal profiles and appear inactive. Their main function is quietly extracting information in bulk.
3. Vanity Metric Bots
Vanity metrics bots artificially inflate the perceived popularity of accounts, pages, or content via fake followers, likes, or comments. They exist to boost social proof.
For example, an influencer may buy thousands of bot followers/engagements to seem more legitimate and influential.
LinkedIn Bot Tactics
Bots use various tactics to infiltrate LinkedIn and achieve their goals:
Aggressive Connection Requests
Spammers leverage bots to send huge volumes of connection invites to random users. Their aim is to get you to unwittingly visit a malicious third-party website.
These bots typically have incomplete profiles and the connection message contains some kind of hyperlink or strange call-to-action.
Comment Spamming
Bots are deployed to blanket high-traffic LinkedIn posts with irrelevant spam backlinks and content. The goal is to drive accidental clicks and increase domain authority via backlinks.
Often these comment spam bots have automatically generated profile pictures and lack any coherent post/work history.
Fake Engagement
Vanity metric bots are programmed to like, share, comment on, and follow target accounts in order to artificially inflate engagement rates. These inflated metrics are then used as “social proof” to entice real users.
hundreds of fake bot accounts will descend upon a target page, artificially driving up follower/engagement stats to improve perceived legitimacy. The client then leverages these inflated metrics as “social proof” when interfacing with potential partners or customers.
Private Message Spam
Similar to aggressive connection requests and comment spam, message spam bots target user inboxes with unsolicited spam links and content. Their infiltration rate tends to be lower thanks to LinkedIn’s algorithmic filters.
These bots typically have sparse connections/experience and messages contain suspicious URLs or weird text copied from the web.
Also Read – Indeed vs LinkedIn, Glassdoor, ZipRecruiter, Monster, and Top Job Sites
Real-World LinkedIn Bot Examples
To appreciate how convincing these malicious bots can be, let’s look at some real-world examples uncovered by genuine LinkedIn users:
Example 1: Recruiter Bot
- Generic stock model profile photo
- Fuzzy background photo
- No shared connections
- The profile photo is inconsistent with the ethnicity implied by the name
- Broken English connection request promising “a wonderful day”

Analysis: Likely a spam bot leveraging the recruiter persona to distribute malicious links or content via messages/connection requests.
Example 2: Sales Bot
- Generic waved hand profile photo
- No experience listed
- Few endorsements despite 500+ connections
- Bio talks about “driving value”
- Comment history full of spammy links

Analysis: Spam bot aiming to backlink comment spam and distribute malware via hyperlinks.
Example 3: Fake Employee Accounts
- Multiple profiles tied to the same company
- Identical canned experience descriptions
- Similar profile/cover photos
- No shared connections
- Seemingly auto-generated endorsements
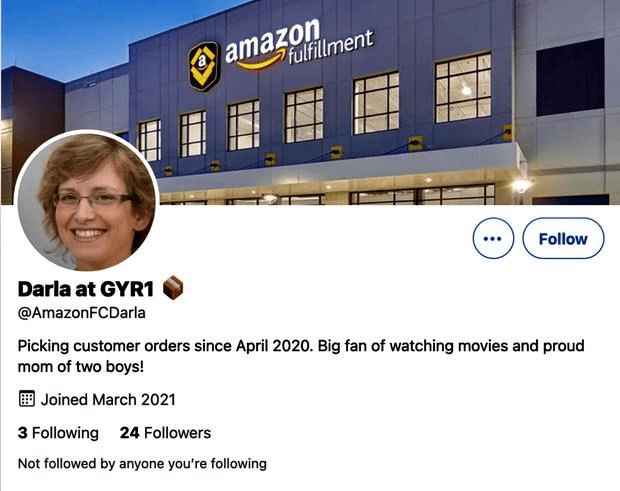
Analysis: Synthetic profiles boost legitimacy via fake employees and manufactured engagement.
As you can see, LinkedIn bots run the gamut from relatively crude spam accounts to sophisticated personas with well-rounded profiles and activity histories. Their common thread is a lack of authenticity under closer scrutiny.
Why are Bots Thriving on LinkedIn?
LinkedIn’s meteoric rise in popularity has attracted bots and bad actors from all corners of the cybercrime underworld. Here are the key reasons malicious bots continue to plague the platform:
Valuable Business Data
LinkedIn member data represents a goldmine for marketers and cybercriminals alike. Names, job titles, skills, company details, etc. can all be exploited for lead generation, credential harvesting, and targeted phishing campaigns.
Powerful Distribution Channel
LinkedIn’s highly engaged professional audience offers unparalleled reach and authority for distributing malicious links, malware, and spam content at scale.
Appearance of Legitimacy
Unlike Facebook or Twitter, LinkedIn users represent real companies and identities. This perceived legitimacy means users more readily click links and engage with seemingly authentic profiles.
Difficult Detection
Bots exploit LinkedIn’s identity-focused format to craft convincing professional personas that easily blend into the business landscape. Spotting fakes among so many genuine accounts is challenging.
Limited Oversight
With over 830 million users sending 4 billion connection requests per week, LinkedIn is likely fighting a losing battle against sophisticated bot networks designed explicitly to emulate human qualities and navigate detection filters.
How to Spot LinkedIn Bot Accounts
Here are 10 tell-tale signals that can help identify bots and fakes infiltrating your LinkedIn network:
1. Few (or no) Shared Connections
Most engagement from strangers with no shared connections should raise suspicions, especially overly familiar language.
2. Suspicious Profile Photos
Fuzzy/generic photos, inconsistent ethnicities, and stock models are common but red flags.
3. Broken English
A mangled grasp of English remains a key bot giveaway in messages and comments from “supposed professionals”.
4. Too Good to be True
Overly complimentary comments or effusive connection requests should make you skeptical of strangers.
5. Strange Behavioral Patterns
Bots betray themselves when connection requests, likes and comments exhibit unusual timing or distribution patterns.
6. URLs in Initial Contact
Any sort of URL included in an unsolicited message or connection request smells rotten.
7. Generic/Contrived Backstories
Sparse work histories and boilerplate background summaries often conceal automation.
8. Sketchy Connection Sources
The mystery increases around how obscure services discovered your profile for targeted connection requests and messages.
9. Minimal Public Activity
Lack of active public engagement beyond shallow comments/likes hints at bots or scrapers. Engagement should align with your interest in your niche and experience level.
10. If It Seems Too Good to Be True…
When something raises your skepticism, go with your gut feeling and investigate further before connecting or clicking anything suspicious.
Alos Read – LinkedIn About Me Examples: Crafting Compelling Profile Summaries
How to Protect Yourself from LinkedIn Bots
Here are 8 proactive tactics to help secure your account against LinkedIn bots and spammers:
1. Tighten Privacy Settings
Restrict who can view your connections, activities, and full profile to reduce bot reconnaissance and spam targeting.
2. Change Notification Settings
Review notification controls to reduce comment/message spam and hide public profile viewing alerts leveraged by data scrapers.
3. Limit Old Connections
Prune ancient connections that may represent dead accounts vulnerable to hijacking by bots and bad actors.
4. Disable LinkedIn on External Services
Revoke permissions that expose your data to third-party apps which can suffer breaches enabling bot infiltration.
5. Report Suspicious Activity
Flag shady profiles and conversations via LinkedIn’s reporting system so their algorithms can adapt.
6. Install a Spam Filter
Consider a browser-based spam filtering extension to automatically hide bogus comments and messages in your LinkedIn feed.
7. DisableMessages From Strangers
Opt to only receive messages from people already in your LinkedIn network to mitigate message spam.
8. Never Click Suspicious Links
However enticing or scary a call-to-action seems, avoid clicking messages or URLs from unverified contacts. Verify legitimacy via independent research before engaging.
Here are step-by-step guides for locking down some key LinkedIn security settings:
How to Restrict LinkedIn Profile Viewing
- Click the ‘Me’ icon in the top nav bar
- Select ‘Settings & Privacy’ > ‘Privacy’
- Under the ‘Profile viewing options’ section, change:
- ‘Your connections’ to ‘Only you’
- ‘Outside of your network’ to ‘Only you’
- Scroll down and click ‘Save’
This hides your profile from public viewing and anonymous scrapes by limiting access to direct 1st-degree connections.
How to Block Linked Messages From Strangers
- Click the ‘Me’ icon in the top nav bar
- Choose ‘Settings & Privacy’
- Select the ‘Communications’ tab
- Under ‘Message Filters’, toggle ‘Receive Messages: Only from people in your network’
- Click ‘Save’ at the bottom
With this filter active, only existing LinkedIn connections can message you directly to prevent cold outreach spam.
How to Remove LinkedIn Data From Data Brokers
- Visit LinkedIn’s data broker removal page
- Enter personal details like name and email
- Confirm account via email verification step
- LinkedIn will now contact listed data brokers on your behalf requesting account data removal
- Click companies to manually review and remove more data as desired
Removing your details from shady data brokers limits external monitoring, targeting, and potential account hijacking by outside parties.
The Future of LinkedIn Bots
Unfortunately, the LinkedIn bot situation will likely continue deteriorating as increasing cybercriminal interest is met with a generally lackluster platform-side response thus far.
Sophisticated deep learning algorithms mean bots are becoming harder to differentiate from genuine users with every passing month. Motivations to weaponize LinkedIn’s professional reach and legitimacy for distributing malware, spam, and disinformation will only intensify across the cybercrime sector.
For now, LinkedIn relies predominantly on user reports to squash bots piecemeal through whack-a-mole style suspensions. But considering the scale of the bot infestation, LinkedIn would do well to bolster its identification capabilities pronto.