With over 300 million active users, Twitter hosts endless conversations and connections. But in enabling communication, Twitter also collects user data for targeted advertising and content recommendations. Balancing open sharing with privacy is an ongoing challenge.
In this comprehensive guide, we’ll explore what data Twitter gathers, the associated risks, and, most importantly – how you Manage Data Sharing in Twitter Privacy Settings and limit data collection where appropriate.
Table of Contents
How Twitter Collects and Uses Your Information
Before diving into privacy controls, let’s look at what data Twitter accumulates and why:
Types of Data Twitter Gathers
Twitter collects a wide range of signals and information about you:
- Account Information: Email/phone number used for signup, username, password, profile bio.
- Content: Tweets, direct messages, photos/videos shared publicly or privately.
- Contacts: Upload address book to find friends or sync LinkedIn.
- Location: Based on device settings, tagged tweets, wifi networks.
- Interests: Follows/likes, tweet engagement, link clicks, topics searched.
- Browsing History: Pages visited, search terms, clicks, scrolling activity.
This data enables Twitter to understand who you are, what you care about, who you interact with, where you go, and how you use their platform.
How Twitter Uses Your Data
Twitter leverages all this intel on users for:
- Personalization: Showing relevant suggestions, topics, accounts, and events based on your interests and activity.
- Advertising: Serving ads aligned to inferred demographics, interests, and habits.
- Content Policies: Identifying prohibited content, spam accounts, misinformation, and abuse.
- Feature Improvement: Understanding how people use Twitter to guide product development.
- Analytics: Tracking overall platform metrics like monthly active users and growth trends.
Your data powers the algorithms that customize and optimize Twitter. It also enables monetization through targeted advertising and insights Twitter sells to partners.
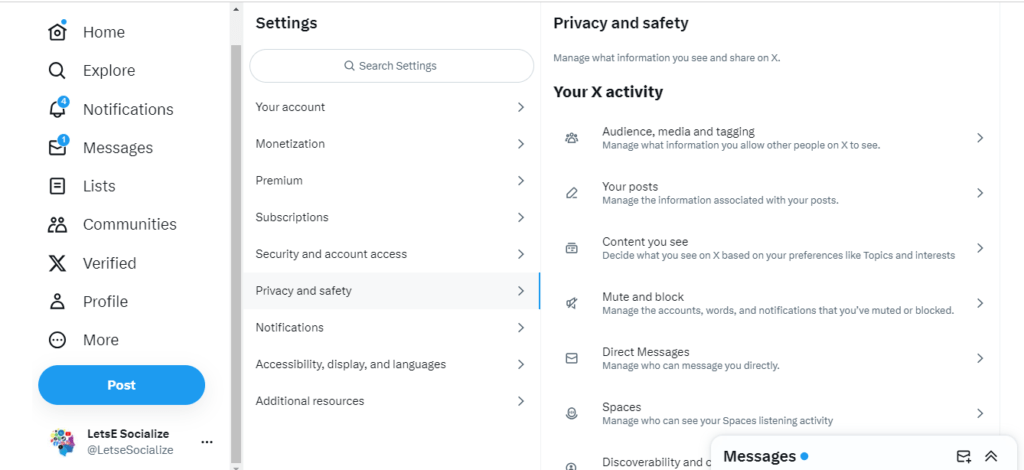
Risks and Concerns Around Twitter’s Data Collection
What are the potential downsides of Twitter’s expansive data gathering?
1. Privacy Invasion
The breadth of data Twitter amasses provides an intimate look at people’s interests, views, identities, and habits without full consent. This can feel like a violation of privacy.
2. Data Exploitation
While Twitter doesn’t sell individual data directly, they monetize it via advertising targeting and analytics. The lack of visibility into these practices leaves users uncomfortable.
3. Security and Hacking
Centralized data collection creates attractive honeypots for cybercriminals. Social media accounts contain a wealth of personal info for identity theft.
4. Account Manipulation
Deep knowledge of user-profiles and psychology allows malicious actors to craft hyper-targeted disinfo, scams, and influence operations.
5. Discrimination
Behavioral profiling and selective ad targeting can enable exclusion or unfair biases based on race, gender, health, age, etc.
6. Chilling Effect
Extensive monitoring can discourage people from engaging openly. Even if not directly misused, pervasive surveillance has a chilling effect.
Overall, users have valid concerns over risks, misuse potential, and lack of oversight into how their data is exploited and secured. It’s sensible to be cautious and limit sharing.
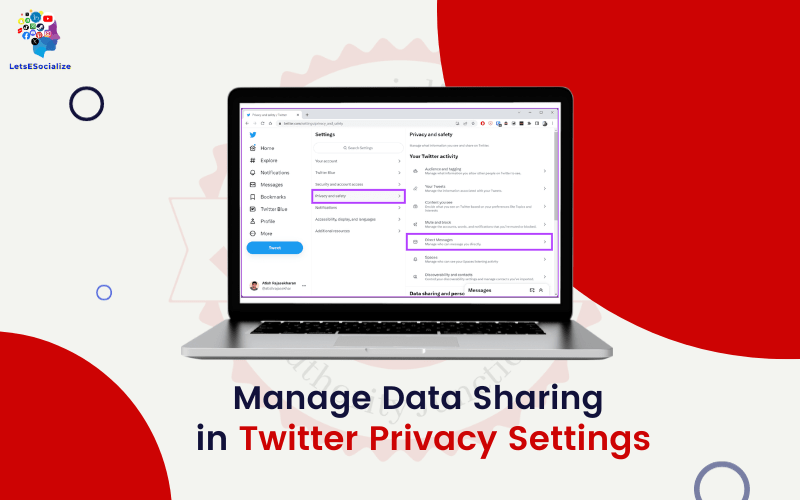
Navigating Twitter Privacy Settings
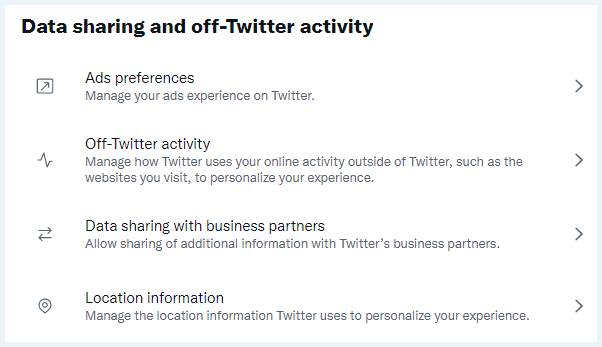
In response to these worries, Twitter does provide a range of privacy controls. However, they are scattered across pages and only sometimes easy to locate. Here’s an overview of key categories and tools to be aware of as you manage settings:
Account Information
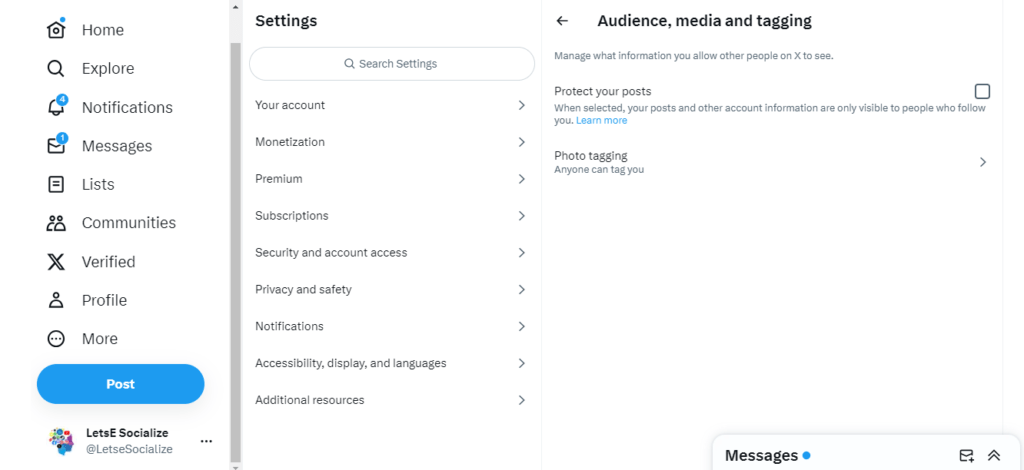
Controls who can see basic profile data like your bio, location, birthday, contacts, and linked accounts. Adjust under:
Settings > Privacy and Safety > Audience and tagging
Tweets
Sets who can see your tweets by default. Options include the public, people you follow, and only people you mention. Adjust under:
Settings > Privacy and Safety > Audience and tagging

Media
Controls who can see photos and videos you share on Twitter. Adjust under:
Settings > Privacy and safety > Audience and tagging
Replies and Mentions
Limits who can mention you in tweets and view your replies. Adjust under:
Settings > Privacy and safety > Audience and tagging
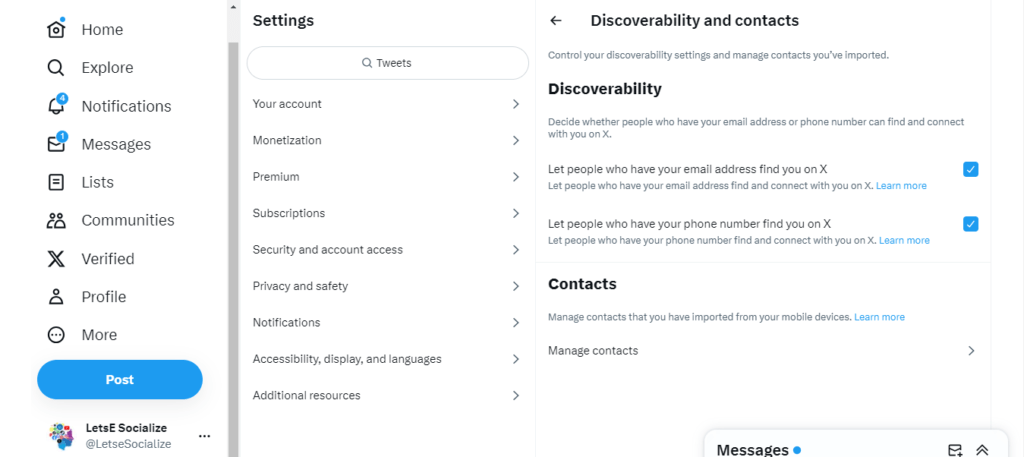
Findability
Opt out of being found by phone number and email search. Adjust under:
Settings > Privacy and safety > Discoverability
Location Info
Review and restrict Twitter’s access to your precise device location. Adjust under:
Settings > Privacy and safety > Location information
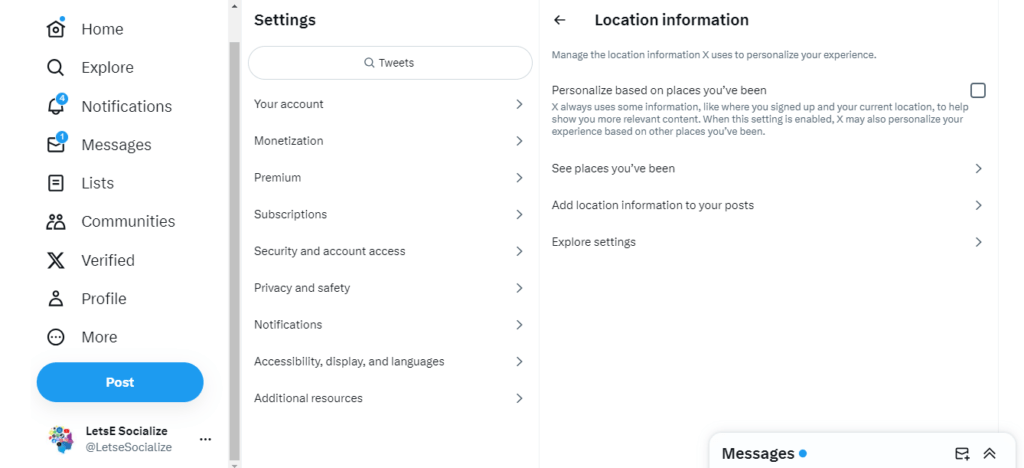
Data Usage
Review how Twitter uses your data for ad targeting and turn off personalized ads. Adjust under:
Settings > Your Twitter data
Third-Party Sharing
See which third-party sites and apps have access to your Twitter data. Adjust under:
Settings > Security and account access > Apps and sessions
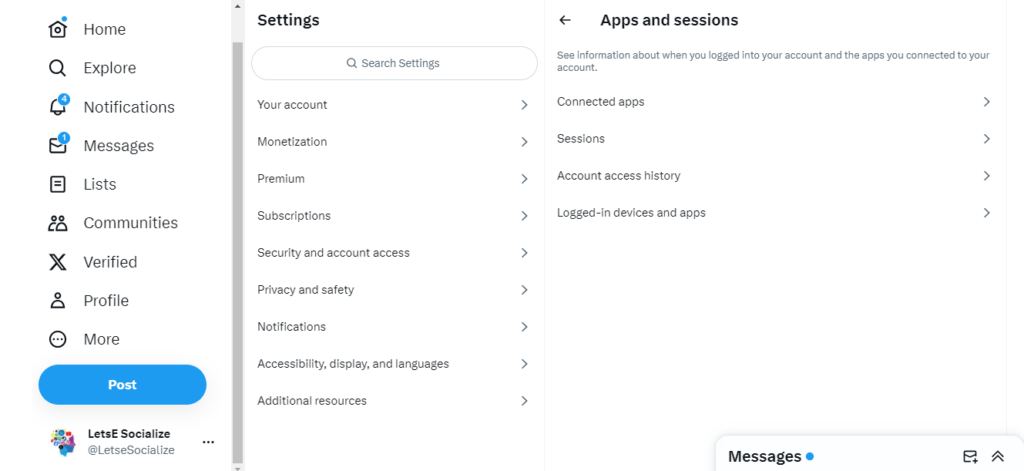
Activity Download
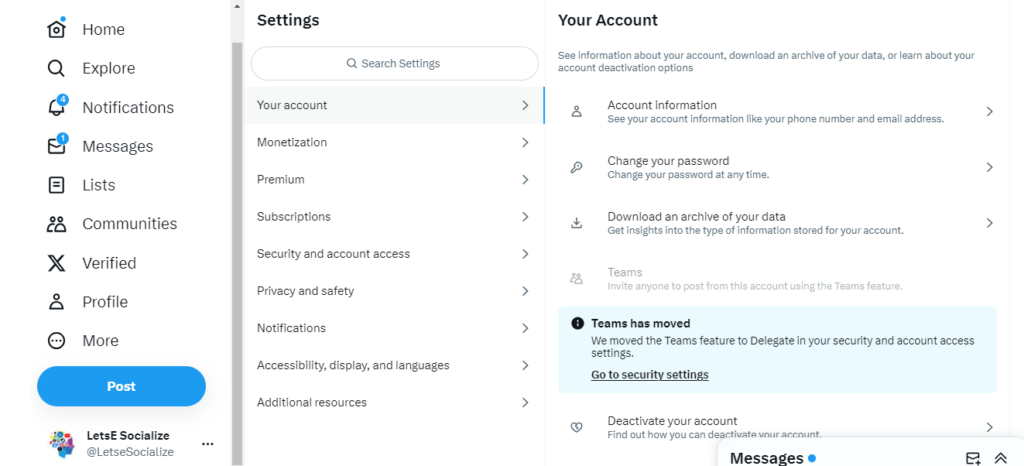
Review an archive of your Twitter data footprint. Adjust under:
Settings > Your account > Download an archive of your data
Take time to thoroughly review each privacy setting category and tailor it based on your comfort level. Like any platform, one size does not fit all regarding optimal privacy controls.
Key Twitter Privacy Settings to Evaluate
While personal preference should drive your settings, a few controls are highly relevant to managing data exposure. Let’s examine them more closely.
Make Accounts Private
The single most comprehensive option is making your Twitter account private via:
Settings > Privacy and safety > Protect your Tweets
This hides your tweets from public view. Follower requests must be approved before someone can access your activity or interact.
It’s a great way to limit visibility from random strangers and prevent content from being surfaced without consent. But reduces opportunities for public engagement, growth, and discovery.
Disable Photo Tagging
Prevent people from tagging you in photos via:
Settings > Privacy and safety > Photo tagging

Photo tags create persistent links between your identity and certain images. Turning off tagging protects associating your account with unapproved content.
Limit Audience for Replies and Mentions
Tailor who can mention you in tweets via:
Settings > Privacy and safety > Audience and tagging
Everyone is the default, but you can limit mentions to only those you follow. Reduces harassment and spam.
Minimize Ad Targeting
Opt out of personalized ads based on your inferred interests:
Settings > Privacy and safety > Ads preferences > Personalized ads
Reduces exploited exposure from ad clicks. But still sees generic ads.
Review Third-Party Apps
Identify who you have authorized to access your Twitter data:
Settings > Security and account access > Apps and sessions
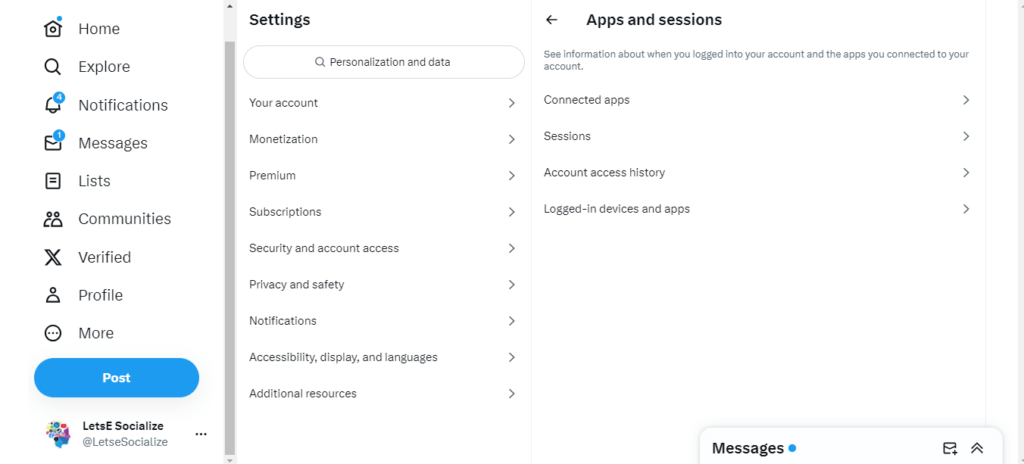
Revoke outdated apps. Be extremely selective in granting third-party access.
The right balance depends on your use case and privacy priorities. However, examining the above key categories equips you to manage data on Twitter better.
Beyond Platform Settings: Ways to Further Limit Twitter Data Sharing
If Twitter’s native controls still leave you uncomfortable, more proactive steps outside the platform itself can further restrict data exposure:
Use Anonymous or Pseudonymous Accounts
Don’t provide your real name, birthdate, contacts, or identifiable info. Make your account untraceable to your identity.
However, reduces personalization and requires constant vigilance not to reveal details that could expose you. Difficult long-term.
Employ a VPN to Mask Your Location
Routing traffic through an intermediary server hides your real IP address and any associated identifiable info.
But VPNs slow performance. Twitter can still deduce general regions from the VPN IP with lower accuracy.
Limit Use of Hashtags
Avoid using identifiable hashtags related to your interests or views. This restricts Twitter from mining your beliefs and affiliations.
However, reduces opportunities for discovery and meaningful connections with kindred voices. Anonymity carries a cost.
Be Cautious About Logging In Through Other Apps
Review permissions carefully before enabling Twitter login through other apps and sites. Avoid granting unnecessary data access.
Frequently Clear Cookies and Cache
Delete browser storage that retains activity history Twitter can mine for data.
However, clearing cookies constantly creates friction and reduces convenience in your experience.
Use Twitter Anonymously Through Tor
The Tor browser routes connections through encryption and randomized nodes, preventing tracking.
The downside is usability barriers. Tor browsing is slow, and Twitter often blocks access from known Tor nodes.
Limit Location Sharing
Disable location tagging, hide your city and avoid mentioning businesses, monuments, or travel spots that reveal your geography.
But reduces local recommendations and context. More than significantly restricting location is needed on mobile devices.
Read Privacy Policies Thoroughly
Study updates to understand changes in how Twitter handles data. Provide feedback on concerning shifts. Know your rights.
However, legal policies are lengthy and complex for average users to parse and act on.
Determined users have paths to minimize exposure beyond relying on platform privacy settings alone. But extra steps require trade-offs in experience and convenience. Managing privacy requires persistence and vigilance.
How Twitter’s Privacy Controls Compare to Other Social Networks
To provide context, how does Twitter stack up against other top social platforms in empowering user data privacy?
| Platform | Privacy Controls Overview |
|---|---|
| Robust set of privacy settings but somewhat difficult to navigate | |
| More limited controls via account type toggles like private; relies on Facebook policies | |
| Most extensive privacy settings given scrutiny but complex to manage | |
| TikTok | Very limited transparency and controls given Chinese regulatory regime |
| Snapchat | Ephemeral sharing reduces risk, settings control discoverability |
| YouTube | Controls limit data collection for ads personalization and pause watch history |
| Touts encryption but still shares metadata with Facebook | |
| Signal | Strongest end-to-end encryption with minimal data access |
Twitter provides users more leverage over data sharing than surveillance-centric platforms like TikTok or ephemeral networks like Snapchat. However, it lacks the robust settings of Facebook. Overall, Twitter falls in the middle of the pack on privacy controls, but UI improvements could make settings more accessible.
Advocacy Calls for Improving Twitter Privacy Practices
While Twitter has gradually enhanced privacy in response to public scrutiny, advocates continue to push for even better policies and controls:
- Granular opt-out of ad targeting: More categories to disable personalized ads via interest, location, engagement, and relationship tracking.
- Indicators when government entities request data: Badge accounts operated by or cooperating with state intelligence agencies.
- Transparency reports on legal data demands: Disclose how often Twitter hands over data to law enforcement and under what circumstances.
- Right to appeal account suspension: Clear process for disputing bans based on speech, copyright, and alleged Terms of Service violations.
- Diversify viewpoint diversity on trust and safety teams: Reduce concentrated internal biases through hiring practices that seek alternate perspectives.
- Algorithmic accountability: External analysis of potential algorithmic biases and harms enabling misinformation, extremism, and manipulation.
- Bug bounty expansion: Compensate security researchers who identify vulnerabilities that could put user data at risk.
- Differential privacy techniques: Add statistical noise to analysis to preserve anonymity at the population level while enabling insights.
- Local data storage requirements: Store user data in the country of origin to prevent international transfers that evade oversight.
Providing users more voice and agency over their data remains critical for Twitter to close the trust gap. Expect advocacy and legal pressure to continue driving the evolution of social media privacy.
Emerging Technologies That Could Disrupt Social Media Data Collection
Looking beyond Twitter to the broader ecosystem, what nascent technologies promise to overhaul how personal data gets exploited?
Cryptocurrency Wallets
Replace centralized credentials like usernames/passwords with blockchain-based decentralized identity management. Enhances security and reduces data aggregation into Honeypots.
Edge Computing
Keep data processing on user devices rather than uploading data to company servers where monetization and misuse risks intensify.
Differential Privacy
Add mathematical noise to datasets to derive insights from populations while preserving the anonymity of individuals.
Federated Learning
Distribute machine learning model training across decentralized devices to prevent raw data pooling. Updates aggregate learnings instead of raw data.
Encrypted Computing
Run computations on fully end-to-end encrypted data via cryptographic techniques like homomorphic encryption and secure multi-party analysis. Eliminates exposing raw data.
Synthetic Data
Train algorithms on artificially generated datasets that mimic real user data without exposing actual people.
Zero Knowledge Proofs
Cryptographically verify credentials or attributes without sharing identifiable raw data.
Data Cooperatives
Rotate control and ownership of personal data from platforms to member-owned data trusts or unions that grant collective oversight.
While still nascent, emerging privacy-enhancing technologies offer hope to reduce exploitative data practices long-term and keep value in user hands rather than companies.
Key Takeaways on Managing Your Twitter Privacy
A few core points to remember about Twitter privacy settings and data sharing:
- Twitter collects extensive personal and activity data for advertising, analytics, and feature personalization.
- Risks like exploitation, manipulation, and discrimination create distrust in how Twitter handles data.
- Twitter offers many privacy controls, but key options like private accounts and limiting ad tracking are most impactful.
- You can restrict data exposure by using anonymous handles, employing VPNs, and clearing cookies and caches.
- Privacy advocacy continues to pressure Twitter to enhance transparency, accountability, and user empowerment.
- Emerging technologies like on-device processing and decentralization provide long-term hope for disrupting current data collection norms.
- Finding the right balance depends on your personal tolerance and regular re-evaluation as threats evolve.
The Bottom Line
Twitter sits at the epicenter of tensions over privacy, authority, and speech across the social web. There are no perfect solutions to balancing safeguards and self-expression.
However, increasing user awareness and control represent important first steps. Corporate responsibility paired with innovation in privacy-enhancing tech offers paths to modernizing practices.
By adjusting your settings, understanding risks, and examining alternatives, you can gain more agency over your data on Twitter. Collective action and diligent advocacy drive progress.
With care, transparency, and constructive debate, societies can advance norms and systems around empowering individuals while supporting connections and commerce in the Digital Age. These challenges are complex but solvable.