In an era where our lives are increasingly intertwined with the digital world, safeguarding our online privacy has become more critical than ever. From social media to online shopping, our personal information is constantly at risk of being exposed or exploited by malicious actors. In this comprehensive guide, 15 Simple Ways to Safeguard Your Online Privacy.
Table of Contents
1. Use Strong, Unique Passwords
I understand the importance of strong, unique passwords. Here are some key points to remember:

Building a Fortress: Strong Passwords
- Length is Strength: The longer the password, the harder it is to crack. Strive for at least 12 characters, but consider going even longer for critical accounts.
- Complexity is Key: Don’t settle for predictable patterns. Mix it up with uppercase and lowercase letters, numbers, and symbols. Avoid using personal information like birthdays or pet names, as these can be easily guessed.
- Uniqueness is Essential: Resist the urge to reuse passwords across different accounts. A data breach on one site could compromise all your accounts if they share the same password.
Going Beyond the Basics
- Embrace Passphrases: Craft a memorable sentence or phrase instead of a single word. Think “ILoveMySecureOnlineLife19!” – strong and easy to recall.
- Password Managers: Your Allies: Remembering numerous unique passwords can be a hassle. Consider using a password manager. These tools securely store your passwords and automatically fill them in when needed.
- Two-Factor Authentication (2FA): Add an extra layer of security with 2FA. Even with a strong password, there’s a risk. 2FA requires a secondary verification step, like a code sent to your phone, to log in.
Remember: Strong, unique passwords are your first line of defense in the digital world. By following these tips, you can create a shield that protects your online accounts and keeps your data safe.
Also Read – Selling Digital Products on Google: A Comprehensive Guide
Also Read – X Embraces Passwordless Future, Gears Up for Passkeys Support on Android
2. Enable Two-Factor Authentication (2FA)
Absolutely! Two-factor authentication (2FA) is a crucial security measure that adds an extra layer of protection to your online accounts. It goes beyond just your password, making it much harder for unauthorized individuals to access your information even if they somehow obtain your password.

Here’s a breakdown of why you should enable 2FA:
- Strength in Layers: Imagine your password as the first lock on your door. 2FA is like adding a deadbolt – an extra hurdle for anyone trying to break in.
- Reduced Hacking Risk: Even strong passwords can be vulnerable to hacking attempts. 2FA makes it significantly more difficult for hackers to gain access, as they would not only need your password but also the additional verification code.
- Peace of Mind: Knowing your accounts have an extra layer of security provides peace of mind. You can relax a bit easier knowing it’s not just your password guarding your data.
Enabling 2FA is usually a straightforward process:
- Log in to your account.
- Navigate to the security settings. This might be labeled “Security” or “Two-factor authentication” depending on the platform.
- Choose your preferred 2FA method. Popular options include:
- Authenticator App: Download an app like Google Authenticator or Microsoft Authenticator on your phone. This app generates unique codes that you’ll need to enter along with your password when logging in.
- SMS Verification: Receive a verification code via text message to your phone number linked to the account.
Here are some additional tips for using 2FA effectively:
- Enable 2FA on all your accounts that offer it. The more accounts you protect, the more secure your overall online presence becomes.
- Consider using a security key for an even stronger authentication method. These physical devices provide a unique code when inserted into your device or tapped against your phone using NFC.
- Don’t share your 2FA codes with anyone. These codes are unique to you and your device and should be kept confidential.
By enabling 2FA and following these practices, you’re significantly strengthening your online security posture. Remember, a little extra effort can go a long way in protecting your valuable data.
3. Keep Software Updated
You’re right! Keeping your software updated is essential for maintaining the security and performance of your devices and applications. Software updates often include patches that fix vulnerabilities or bugs that hackers can exploit to access your system or data. Here’s why keeping your software updated is so crucial:

- Enhanced Security: Updates frequently address security vulnerabilities identified by developers. By installing them, you’re essentially plugging holes in your system’s defenses, making it much harder for hackers to gain unauthorized access.
- Improved Performance: Updates can address bugs that cause crashes, slowdowns, or other performance issues. A smooth-running system is not only frustration-free but can also be more efficient.
- New Features and Functionality: Updates sometimes introduce new features and functionalities that enhance the capabilities of your software. You might gain access to improved productivity tools, compatibility with new hardware, or additional security features.
- Compatibility: Outdated software may eventually become incompatible with newer versions of other programs or operating systems. Keeping things updated ensures everything works together seamlessly.
Here are some tips for keeping your software updated:
- Enable automatic updates: Most software and apps offer the option to automatically download and install updates as soon as they become available. This is the easiest way to stay up-to-date and avoid the risk of forgetting to update manually.
- Schedule regular checks: If you prefer manual updates, set a reminder to check for updates on your operating system, software programs, and apps periodically. Weekly or bi-weekly checks are a good starting point.
- Update all your software: Don’t just focus on your operating system. Update all the software programs and apps you use regularly, including web browsers, media players, productivity tools, and security software.
Here are some additional things to keep in mind:
- Be cautious of suspicious update prompts: Software updates typically come from the official source of the software you’re using. Be wary of clicking on update prompts from unknown websites or emails, as these could be phishing attempts designed to install malware on your device.
- Back up your data: Before installing any major software update, it’s always a good practice to back up your important data. In the rare case that something goes wrong during the update process, you’ll have a safe copy of your information.
By keeping your software updated, you’re taking a proactive approach to securing your devices and data. It’s a simple yet highly effective way to safeguard yourself from online threats and ensure your software functions optimally.
4. Use a Virtual Private Network (VPN)
In today’s digital world, where privacy and security are paramount, a Virtual Private Network (VPN) emerges as a valuable tool. A VPN encrypts your internet traffic and routes it through a remote server, essentially creating a secure tunnel between your device and the internet. Let’s delve into the advantages of using a VPN:

1. Enhanced Security:
- Encryption Powerhouse: A VPN encrypts your data, making it unreadable to anyone snooping on your internet connection. This is especially important on public Wi-Fi networks, where your data is vulnerable to interception.
- Cloaking Your Online Activity: With a VPN, your internet traffic appears to originate from the VPN server’s location, masking your actual IP address. This provides an extra layer of anonymity online.
2. Bypassing Geo-Restrictions:
- Content Without Borders: Certain websites or streaming services may be geo-restricted, meaning they’re only accessible from specific countries. A VPN allows you to connect to a server in a different location, granting you access to content that might otherwise be unavailable.
- Censorship Circumvention: In countries with internet censorship, a VPN can be a valuable tool to access blocked websites and information. However, it’s important to be aware of local laws and regulations regarding VPN use.
3. Increased Privacy:
- Shielding Your Browsing Habits: A VPN helps shield your browsing activity from your internet service provider (ISP) or any third-party trackers. This means your ISP can’t monitor the websites you visit or collect data about your online behavior.
- Enhanced Anonymity: When you use a VPN, websites and online services see the VPN server’s IP address instead of your own. This makes it more difficult for them to track your online movements and build a profile on you.
4. Additional Considerations:
- Choose a Reputable VPN Provider: The quality of VPN services varies considerably. Opt for a reputable provider with a strong track record in security and privacy.
- Potential Performance Impact: VPNs can sometimes add slight latency (delay) to your internet connection. This is usually negligible for basic browsing but might be more noticeable for activities like online gaming or downloading large files.
In conclusion, a VPN can be a powerful tool for enhancing your online security, privacy, and freedom. By understanding its benefits and considering potential trade-offs, you can determine if a VPN is the right choice for your digital needs.
5. Be Cautious on Public Wi-Fi Networks
Absolutely! Public Wi-Fi networks, while convenient, can be breeding grounds for security risks. Here’s why you should exercise caution when connecting to them:

Unsecured Connections: Public Wi-Fi networks are often open and unencrypted. This means your data travels unscrambled, making it vulnerable to interception by hackers lurking on the network.
Man-in-the-Middle Attacks: Malicious actors can set up fake Wi-Fi hotspots that mimic legitimate ones. If you connect to such a network, they could potentially steal your login credentials, personal information, or financial data.
Snooping and Data Theft: Anyone on the same public Wi-Fi network could potentially snoop on your unencrypted traffic. This could include passwords, emails, browsing history, or even messages you send or receive online.
Here are some essential tips for staying safe on public Wi-Fi:
- Avoid sensitive activities: If possible, refrain from accessing online banking accounts, making online purchases, or entering any sensitive information while connected to public Wi-Fi.
- Use a VPN: A Virtual Private Network encrypts your internet traffic, creating a secure tunnel between your device and the internet. This significantly reduces the risk of your data being intercepted on a public network.
- Limit what you share: Be mindful of what information you share on public Wi-Fi. Avoid logging in to social media accounts or accessing confidential documents unless necessary.
- Disable file sharing: On your device’s Wi-Fi settings, ensure file sharing is disabled to prevent unauthorized access to your local files.
- Use a mobile hotspot (if available): Consider using your mobile phone’s hotspot feature to create a secure internet connection for your device, especially if you need to access sensitive information.
- Keep software updated: Ensure your operating system, web browser, and security software are up-to-date to benefit from the latest security patches.
By following these precautions, you can significantly reduce the risks associated with using public Wi-Fi. Remember, a little extra caution can go a long way in protecting your data and privacy online.
6. Review Privacy Settings on Social Media Platforms
In the age of social media, where we share a significant part of our lives online, reviewing privacy settings on these platforms is crucial. Just like adjusting the blinds in your physical home, social media privacy settings allow you to control who sees what information you share. Here’s why you should regularly review and adjust your privacy settings:
1. Shielding Your Personal Information:
- Control Your Profile Visibility: Decide who can see your profile information, including your posts, photos, and even your friend list. You can choose to keep your profile private or limit visibility to friends, friends of friends, or specific groups you create.
- Taming Targeted Advertising: Social media platforms use your information to target you with ads. Review your privacy settings to limit the data they collect and use for advertising purposes.
2. Managing Who Can Contact You:
- Curbing Unwanted Messages: Social media platforms can be breeding grounds for spam or unwanted messages. Privacy settings allow you to control who can send you direct messages or friend requests.
- Location Sharing: Be mindful of location-sharing features. You can choose to disable location sharing entirely or control which posts include your location information.
3. Understanding App Permissions:
- Guarding Your Data: Social media apps often request access to various features on your device, like your location or camera. Review app permissions and grant access only to features necessary for the app to function properly.
Here’s a step-by-step approach to reviewing your privacy settings:
- Locate the Settings Menu: This is typically found in the account dropdown menu or a gear icon within your social media app.
- Explore the Privacy Options: Each platform has differently named sections, but you’ll find options related to profile privacy, information sharing, location settings, and app permissions.
- Adjust According to Your Comfort Level: Decide who you want to see your information and what data you’re comfortable sharing with the platform or third-party apps.
Remember: Privacy settings are not set in stone. Review them periodically as platforms update their features or your comfort level evolves. Taking control of your social media privacy empowers you to curate the online experience you desire.
7. Limit Sharing Personal Information Online
Absolutely! In today’s digital age, it’s more important than ever to be mindful of the personal information we share online. Oversharing can have some consequences, so here’s why you should be cautious about what you reveal:

1. Privacy Breaches and Identity Theft:
- The more information you share online, the bigger the target you create for potential scammers and identity thieves. Personal details like your birth date, address, or Social Security number (even partial digits) can land in the wrong hands if not handled carefully.
2. Damage to Your Reputation:
- Remember, the internet has a long memory. Things you post online today could come back to haunt you later in life, potentially affecting your employment prospects, educational opportunities, or even personal relationships.
3. Targeted Scams and Social Engineering:
- Criminals can exploit the information you share online to craft personalized scams. For example, knowing your birthday or hometown allows them to create phishing attempts that appear more believable.
4. Digital Footprint Management:
- The information you share online contributes to your digital footprint, which is essentially a collection of your data scattered across the web. An excessive digital footprint can make it difficult to maintain control over your online presence and reputation.
Here are some tips for limiting the personal information you share online:
- Think Before You Post: Ask yourself if the information you’re about to share is truly necessary. If not, err on the side of caution and keep it private.
- Beware of Oversharing on Social Media: Review your privacy settings on social media platforms and limit the information visible to everyone.
- Be Wary of Online Quizzes and Surveys: These can often be designed to collect personal information under the guise of entertainment.
- Separate Your Online Personas: Consider using different usernames and email addresses for professional and personal accounts.
- Use Strong Passwords and Be Cautious of Phishing Attempts: Don’t reuse passwords across different platforms and be wary of emails or messages requesting sensitive information.
By following these tips, you can take control of your online privacy and minimize the risk of sharing more information than you intend. Remember, a healthy dose of caution goes a long way in protecting yourself in the digital world.
8. Encrypt Your Communications
In the digital age, where information travels at lightning speed, protecting your communications is paramount. Encryption acts as a digital clock, scrambling your messages and data to ensure only authorized recipients can access them. Here’s why encrypting your communications is a wise security practice:
1. Confidentiality: Building a Digital Vault
- Encryption safeguards the privacy of your communications. Imagine sending a letter sealed with a wax stamp and a unique emblem – only the intended recipient with the matching emblem can break the seal and read the message. Encryption functions similarly, ensuring only authorized parties with the decryption key can understand your messages.
2. Combating Interception: Outsmarting Eavesdroppers
- Our online world is full of potential eavesdroppers. Hackers might lurk on public Wi-Fi networks, and even internet service providers (ISPs) could potentially monitor unencrypted traffic. Encryption scrambles your data, making it indecipherable to anyone without the decryption key, rendering eavesdropping futile.
3. Securing Sensitive Information:
- When transmitting sensitive information like financial data, login credentials, or confidential business documents, encryption becomes imperative. Encryption safeguards this sensitive data, minimizing the risk of it falling into the wrong hands in case of a security breach.
4. Methods of Encryption: Choosing Your Digital Shield
There are various encryption methods available, each with its strengths and uses. Common options include:
- Transport Layer Security (TLS): This widely used protocol encrypts communication between your web browser and a website, protecting data during online transactions or login processes.
- Virtual Private Networks (VPNs): VPNs encrypt all your internet traffic, creating a secure tunnel between your device and the internet.
- Signal Messaging App: This popular app offers end-to-end encryption for your messages and calls, ensuring only you and the recipient can access the content.
Here are some additional points to consider:
- Understanding Encryption Levels: The complexity of encryption algorithms determines the level of security. Stronger encryption is generally more secure but may require more processing power.
- Finding the Right Balance: While robust encryption is ideal, consider the trade-off between security and convenience. For casual conversations, basic encryption might suffice, while stronger methods are recommended for highly sensitive information.
By incorporating encryption practices into your online routine, you can significantly enhance the security of your communications. Remember, a little effort goes a long way in safeguarding your privacy and protecting your confidential data in the vast digital landscape.
9. Use Privacy-Focused Search Engines
In the age of data collection and targeted advertising, privacy-focused search engines have emerged as a valuable alternative to mainstream options. These search engines prioritize user privacy by not tracking your searches, building profiles, or bombarding you with personalized ads. Here’s why considering a privacy-focused search engine might be a good fit for you:

1. Reclaiming Your Search Privacy:
- Free from Tracking: Unlike traditional search engines that monitor your searches and browsing habits, privacy-focused options don’t track your queries. This means your search history remains private, and you’re not being profiled to receive targeted ads.
- Neutral Search Results: Without the influence of your search history or online behavior, privacy-focused search engines aim to deliver unbiased and neutral results. This allows you to see a broader range of viewpoints and information, potentially leading to more well-rounded research or discovery.
2. Enhanced Security:
- Guarding Your Data: Privacy-focused search engines typically don’t store your personal information like IP address or location data. This minimizes the risk of data breaches and protects your online anonymity.
- HTTPS Connections: Many privacy-focused search engines prioritize secure connections using HTTPS protocol. This encrypts your search queries, adding an extra layer of security and making it more difficult for hackers to intercept your information.
3. Some Popular Options:
- DuckDuckGo: A widely recognized privacy-focused search engine offering a clean interface and features like bang searches to explore specific websites directly.
- Startpage: This unique option anonymizes your searches by routing them through Google’s servers while still protecting your privacy by not tracking or storing your data.
4. Things to Consider:
- Search Accuracy: Since privacy-focused search engines don’t personalize results, they might not always be as tailored to your specific needs compared to traditional search engines.
- Limited Features: Some privacy-focused search engines may offer fewer additional features compared to mainstream options.
Overall, privacy-focused search engines provide a valuable alternative for users who prioritize online privacy and unbiased search results. While they may have some trade-offs in terms of personalization and features, the privacy benefits they offer can be a significant advantage for security-conscious users.
10. Clear Browser Cookies and History Regularly
You’re right! Regularly clearing your browser cookies and history is a good practice for maintaining some level of privacy and improving your browsing experience. Here’s a breakdown of why:
1. Enhanced Privacy:
- Controlling Your Digital Footprint: Cookies, small data files stored on your device by websites, can track your browsing activity. Regularly clearing them helps limit the information websites can gather about you.
- Reduced Tracking: Cookies are often used for targeted advertising. Clearing them can help reduce the feeling of being tracked online and bombarded with ads based on your browsing history.
2. Improved Performance:
- A Clean Slate for Browsing: Over time, cookies and browsing history can accumulate, potentially slowing down your browser. Clearing them occasionally can help your browser run more efficiently.
- Fixing Website Issues: Sometimes, outdated cookies or cached data can cause websites to malfunction. Clearing them can resolve these issues and ensure websites load properly.
3. When to Consider Clearing:
- After Public Wi-Fi Use: It’s a good idea to clear your cookies and history after using public Wi-Fi, especially if you access any sensitive accounts.
- Frequent Login Issues: If you’re experiencing frequent login issues on websites, clearing cookies can sometimes resolve the problem.
- Maintaining Privacy Preferences: If you’ve opted out of website tracking or disabled personalized ads, clearing cookies can help enforce these preferences.
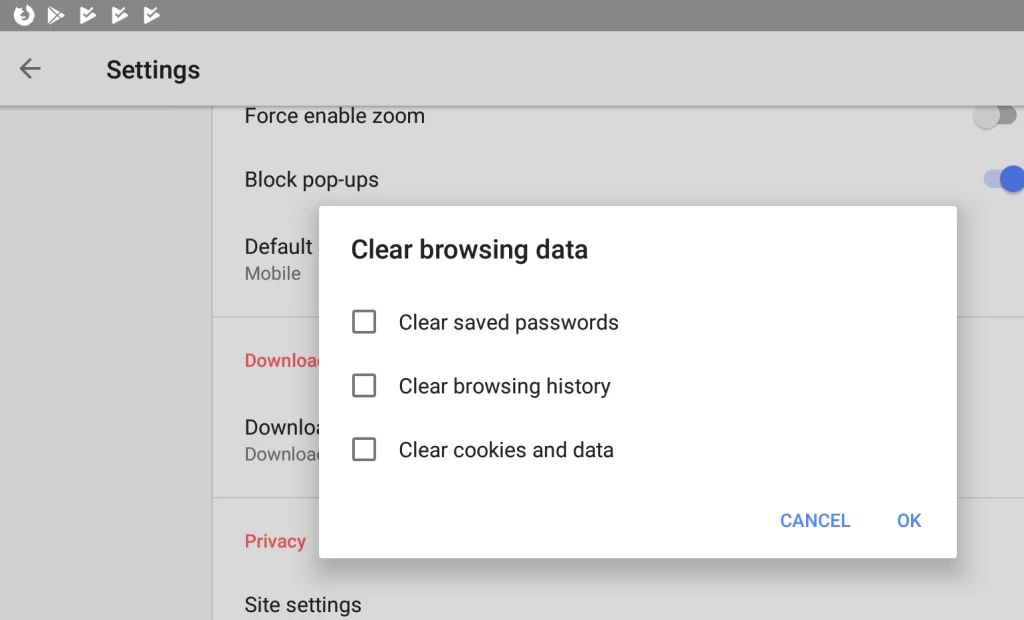
Here’s how to clear cookies and history on the most popular browsers:
- Google Chrome: Click the three vertical dots in the top right corner, and go to Settings > Privacy and security > Clear browsing data. Choose the desired time range and select “Cookies and other site data” and “Cached images and files” before clicking “Clear data.”
- Mozilla Firefox: Click the three horizontal lines in the top right corner, go to History > Clear Recent History. Choose the desired time range and select “Cookies” and “Cached Web Content” before clicking “Clear Now.”
- Microsoft Edge: Click the three horizontal dots in the top right corner, go to Settings > Privacy, search, and Services> Clear browsing data. Choose the desired time range and select “Cookies and other site data” and “Cached images and files” before clicking “Clear now.”
Remember, clearing cookies and history has some drawbacks:
- You’ll Need to Re-login: You’ll likely need to re-enter login credentials for websites you’ve accessed before.
- Loss of Preferences: Some websites may forget your preferences, like language or location settings.
Overall, regularly clearing your browser cookies and history is a relatively simple way to gain some control over your online privacy and potentially improve your browsing experience. Weigh the benefits against the drawbacks to determine how often this practice fits your browsing habits.
11. Beware of Phishing Attempts
You’re right! Phishing attempts are a major threat in the digital world, so staying vigilant is crucial. Phishing scams aim to trick you into revealing personal information or clicking malicious links. Here’s why you should beware of phishing attempts:

1. Disguised Deception:
- Mimicking Legitimate Sources: Phishing emails or messages often appear to be from familiar senders like banks, credit card companies, or even social media platforms. They may use logos, fonts, and language that closely resemble the real organization to deceive you.
2. Urgency and Fear Tactics:
- Creating a Sense of Panic: Phishing messages often try to create a sense of urgency or fear. They might warn of account suspension, unpaid bills, or security risks, pressuring you to take immediate action without thinking critically.
3. Tricks to Steal Your Information:
- Phishing for Credentials: Phishing attempts often include malicious links that lead to fake login pages designed to steal your usernames, passwords, and other sensitive information.
- Beware of Attachments: Phishing emails might contain infected attachments that, once downloaded, can install malware on your device, compromising your security and privacy.
Here are some tips to avoid falling victim to phishing attempts:
- Scrutinize Sender Emails: Don’t just rely on the sender name. Carefully examine the email address for any inconsistencies. A legitimate bank wouldn’t send an email from a free email service provider like Gmail or Yahoo Mail.
- Don’t Click Suspicious Links: Hover over links before clicking to see the actual web address. If it looks suspicious or different from what’s displayed in the text, don’t click on it.
- Verify Information Directly: If a message claims to be from a legitimate organization, contact them directly through their official website or phone number to verify the information before taking any action.
- Be Wary of Unexpected Attachments: Don’t download or open attachments from unknown senders or emails you weren’t expecting.
Remember, if something seems too good to be true, it probably is. Financial institutions or social media platforms won’t pressure you to take immediate action through email. By staying cautious and verifying information, you can significantly reduce the risk of falling victim to a phishing scam.
Is there anything else you’d like to know about online security or privacy?
12. Secure Your Devices
Securing your devices is an essential part of protecting yourself online. Here’s a breakdown of key areas to focus on:

Software Updates:
- Patching Up Vulnerabilities: Software updates often include security patches that address vulnerabilities discovered by developers. These vulnerabilities could potentially be exploited by hackers to gain access to your device or data. Always install updates for your operating system, web browser, apps, and security software as soon as they become available.
Strong Passwords and Authentication:
- Building a Fortress: Use strong, unique passwords for all your online accounts. Avoid easily guessable patterns and don’t reuse passwords across different platforms. Consider using a password manager to generate and store secure passwords.
- Two-Factor Authentication (2FA): Enable 2FA whenever possible. This adds an extra layer of security by requiring a second verification code, like one sent to your phone, in addition to your password when logging in.
Antivirus and Anti-Malware Protection:
- Digital Bodyguards: A reputable antivirus and anti-malware program can help detect and block malicious software that could harm your device or steal your data. Keep your antivirus software updated to ensure it can identify the latest threats.
Firewalls:
- Guarding Your Digital Gate: A firewall acts as a barrier between your device and the internet, monitoring incoming and outgoing traffic. It can help block unauthorized access attempts and prevent malware from infiltrating your system.
Physical Security:
- Safeguarding Your Device: Don’t leave your devices unattended in public places. Enable screen lock features with strong passwords or PINs to prevent unauthorized access if your device is lost or stolen.
Encryption:
- Data Confidentiality: Consider encrypting sensitive data on your devices. This can add an extra layer of security, making it difficult for unauthorized individuals to access your data even if they gain physical possession of your device.
Here are some additional points to consider:
- Be Wary of Downloading from Unknown Sources: Only download apps and software from trusted sources like official app stores. Avoid downloading attachments or clicking on links from unknown senders.
- Public Wi-Fi Precautions: Be cautious when using public Wi-Fi networks. Avoid accessing sensitive information or online accounts while connected to public Wi-Fi. Consider using a VPN (Virtual Private Network) for added security on public networks.
By following these practices, you can significantly strengthen the security of your devices and protect yourself from online threats. Remember, online security is an ongoing process, so stay informed and adapt your practices as technology evolves.
13. Be Selective with App Permissions
You’re right! Being selective with app permissions is crucial for maintaining control over your data and privacy on your devices. Apps often request access to various features and information on your device, and it’s important to understand why they need it and decide if granting access is truly necessary.

Here’s why you should be mindful of app permissions:
- Privacy Concerns: Granting unnecessary permissions can expose your personal information or device functionalities to apps. For example, a photo editing app might not need access to your location data.
- Security Risks: Malicious apps can exploit permissions to steal information, install malware, or even track your activity. Being selective helps minimize these risks.
- Battery Drain: Certain permissions, like location services, can drain your battery life. Limiting unnecessary permissions can help conserve battery power.
Here are some tips for being selective with app permissions:
- Review Permissions Before Downloading: Many app stores display the permissions an app requires before you download it. Review this information carefully and consider if the permissions seem reasonable for the app’s functionality.
- Don’t Grant All Permissions Automatically: When installing an app, take the time to review each permission request and only grant access to what’s truly necessary for the app to function properly.
- Check Permissions Regularly: Even after installing an app, you can usually review and adjust the permissions it has been granted within your device’s settings menu. This allows you to revoke access if you find it unnecessary.
Here are some additional things to consider:
- Understanding Different Permission Categories: App permission categories can vary depending on your device and operating system. Familiarize yourself with the different categories (e.g., location, camera, microphone) to understand what kind of data each permission grants access to.
- Alternatives for Sensitive Permissions: If an app requests permission that seems excessive for its functionality, consider if there are alternatives. For example, if a photo editing app wants location access, you might be able to use the app without granting that permission.
By being selective with app permissions, you take control of your privacy and security. Remember, you don’t have to give apps access to everything they request. Grant permissions judiciously and review them periodically to maintain control over your data and device functionalities.
14. Read Privacy Policies Carefully
You’re right! Reading privacy policies carefully is an important step toward understanding how companies collect, use, and share your data. While they may not be the most exciting reading material, privacy policies contain crucial information about your privacy rights.

Here’s why you should make an effort to read privacy policies:
- Understanding Data Practices: Privacy policies disclose what data a company collects about you, how they use it, and with whom they might share it. This knowledge empowers you to make informed decisions about using their services.
- Transparency and Control: Privacy policies can reveal if a company sells your data to third parties or uses it for targeted advertising. Being aware of these practices allows you to potentially adjust your privacy settings or opt out of data sharing if you prefer.
- Knowing Your Rights: Privacy policies often outline your rights regarding your data. This might include the ability to access, correct, or delete your information. Understanding these rights empowers you to take control of your data privacy.
While privacy policies can be lengthy and filled with legalese, here are some tips for navigating them effectively:
- Look for Key Sections: Focus on sections like “Data Collection,” “Data Use,” and “Data Sharing” to understand what data is collected, how it’s used, and with whom it’s shared.
- Ctrl+F is Your Friend: Use the find function (Ctrl+F on PC) to search for specific keywords that interest you, such as “location data” or “targeted advertising.”
- Seek Clarification: If something is unclear or you have questions about specific practices, don’t hesitate to contact the company directly.
Here are some additional points to consider:
- Privacy Policy Updates: Privacy policies are subject to change. Be mindful of occasional updates and review them to stay informed about any modifications to a company’s data practices.
- No Privacy Policy, No Service: If a service or app doesn’t have a disclosed privacy policy, it’s a red flag. Consider using an alternative service that respects user privacy and transparency.
By taking the time to read privacy policies, you can gain valuable insights into how companies handle your data. This knowledge empowers you to make informed choices and protect your privacy online. Remember, your data is valuable, so understanding how it’s being used is crucial.
Also Read – Facebook Shop vs Google Shop: Unveiling the Differences in the E-Commerce Battle
Also Read – Twitter Faces Backlash for Lack of Calling Options
15. Stay Informed and Educated
Absolutely! Staying informed and educated is critical in the ever-evolving landscape of online security and privacy. Here’s why staying current is essential:

- The Threat Landscape Shifts Constantly: New hacking techniques, malware variants, and phishing scams emerge all the time. By staying informed about the latest threats, you can adapt your security practices to stay ahead of the curve.
- Technology Advances Create New Challenges: As technology progresses, so do the ways our data is collected and used. Keeping up-to-date on these developments allows you to understand the potential privacy implications and make informed decisions about using new technologies.
- Empowerment Through Knowledge: The more you understand about online security and privacy, the better equipped you are to protect yourself. Knowledge is power, and it empowers you to make conscious choices about your online activities and safeguard your data.
Here are some resources to help you stay informed:
- Reputable Cybersecurity Websites: Websites maintained by security organizations or reputable news sources often publish articles and guides on current threats, best practices, and security tips.
- Government Resources: Many government agencies have dedicated sections on their websites that provide information on online safety and security.
- Tech Blogs and Publications: Tech blogs and publications often cover security topics and offer insights from security experts.
- Security Software Providers: Security software providers frequently publish blog posts and articles on the latest threats and how to stay safe online.
Here are some additional tips for staying informed:
- Follow Security Experts on Social Media: Many security experts and organizations maintain active social media presence and share valuable information and updates.
- Attend Webinars or Online Courses: Several organizations and platforms offer free or paid webinars and online courses on cybersecurity and online privacy.
- Make Security a Habit: Dedicate some time each week or month to catching up on the latest security news and trends. This way, it becomes a habitual part of your online routine.
Remember, staying informed is an ongoing process. By dedicating some time and effort to learning about online security and privacy, you can significantly enhance your ability to protect yourself in the digital world. The more you know, the safer you’ll be!
Conclusion
By implementing these 15 strategies, you can significantly enhance your online privacy and security while navigating the internet. Remember to stay vigilant, stay informed, and take proactive steps to safeguard your personal information in today’s digital landscape.







